This document lists the security requirements that are applicable for healthcare software systems integrating with the My Health Record system.
The profile includes two main sections:
- Conformance requirements that apply to the healthcare software system
- Compliance requirements that apply to the software provider organisation.
Important UpdateWe are sharing a few document artefacts have been uplifted to provide clearer guidance on processes, requirements, and formatting. This is to support software developers in planning and implementing changes. Please familiarise yourself with the refreshed artefacts:
NOTE: The core MHR Connecting Systems Security Conformance Profile v1.0.1 requirements remain unchanged from version 1.0 |
The Agency is cognisant of the inherent cyber security risks posed by systems connected to and accessing the My Health Record system, as well as potentially vulnerable aspects of the national infrastructure and all services under its care. To address this risk, a set of security requirements for systems connecting to the My Health Record system have been identified. The controls that are most relevant to the development of software for healthcare organisations, have been selected from the Australian Cyber Security Centre’s Information Security Manual (ISM).
The focus of this conformance profile is on incorporating the security control functionalities within software systems that are connected to the My Health Record system either directly or indirectly. This conformance profile sets a minimum standard or baseline level of cyber security that is expected of connecting systems, and that is consistently adopted. The requirements in this conformance profile are intended to strike an appropriate balance between strengthening the cyber security posture of all connecting systems and minimising potential impacts on software providers and overall system participation. In doing so, this conformance profile supports the overarching goals of improving security within healthcare software systems and fostering a secure and trusted healthcare ecosystem.
Benefits of the new security requirements:
The new requirements ensure that software developers of connected clinical information systems:
- reduce the likelihood of cyber-attacks by disabling redundant technologies
- strengthen system authentication and application timeouts
- use contemporary encryption methods
- perform third-party security testing (penetration testing and vulnerability testing)
- reduce the risk of security vulnerabilities by keeping software up to date (patching)
- securely back up personal and clinical information.
Conformance steps
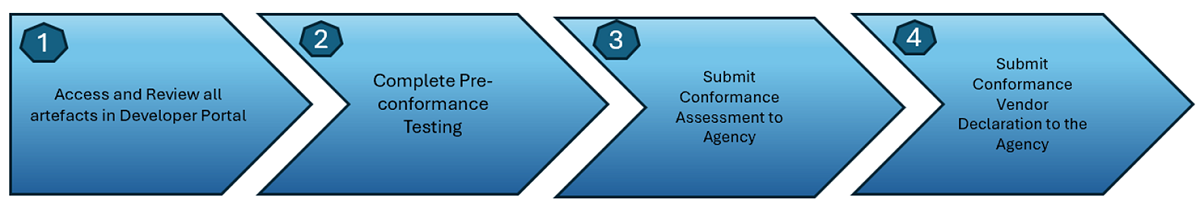
The below table describes the activities for each step of the conformance process.
| Process Activity | Description/Action |
|---|---|
|
|
|
|
|
Send an email to help@digitalhealth.gov.au with the following information:
Upload the following documents for Conformance Assessment:
|
|
Submit the following documents for Conformance Declaration.
|
Questions and further information
Visit:
- My Health Record Connecting Systems Security Conformance Profile - Frequently Asked Questions (FAQ)
- My Health Record Connecting Systems Security Conformance Profile Implementation Timeline
Contact us:
If you require assistance during any stage of this process, please email the Agency at help@digitalhealth.gov.au