Quick intro
Many of the PCA™ API operations can be accessed by applications with the authorisation of their currently logged in user.
The following summarizes the user-based authorisation mode of accessing the PCA™ API:
- Applications (i.e. ClientSystems) obtain PCA™ API OAuth 2.0 access tokens from the PCA™ Identity and Access Manager using the OAuth 2.0 “authorization_code” grant type.
- The PCA™ Identity and Access Manager issues PCA™ API access tokens which are only valid for a limited time – no refresh tokens are issued. Clients must delete them when the user session is no longer active
The figure shows the user-based authorisation pattern for the case where the ClientSystem has its own local user identity and authorisation implementation. In this case a local user session, hosted by the ClientSystem, is established in step 1 – but the user is then required to authenticate separately to PRODA for the PCA API access tokens to be issued to the PCA Web Application (steps 2 to 14).
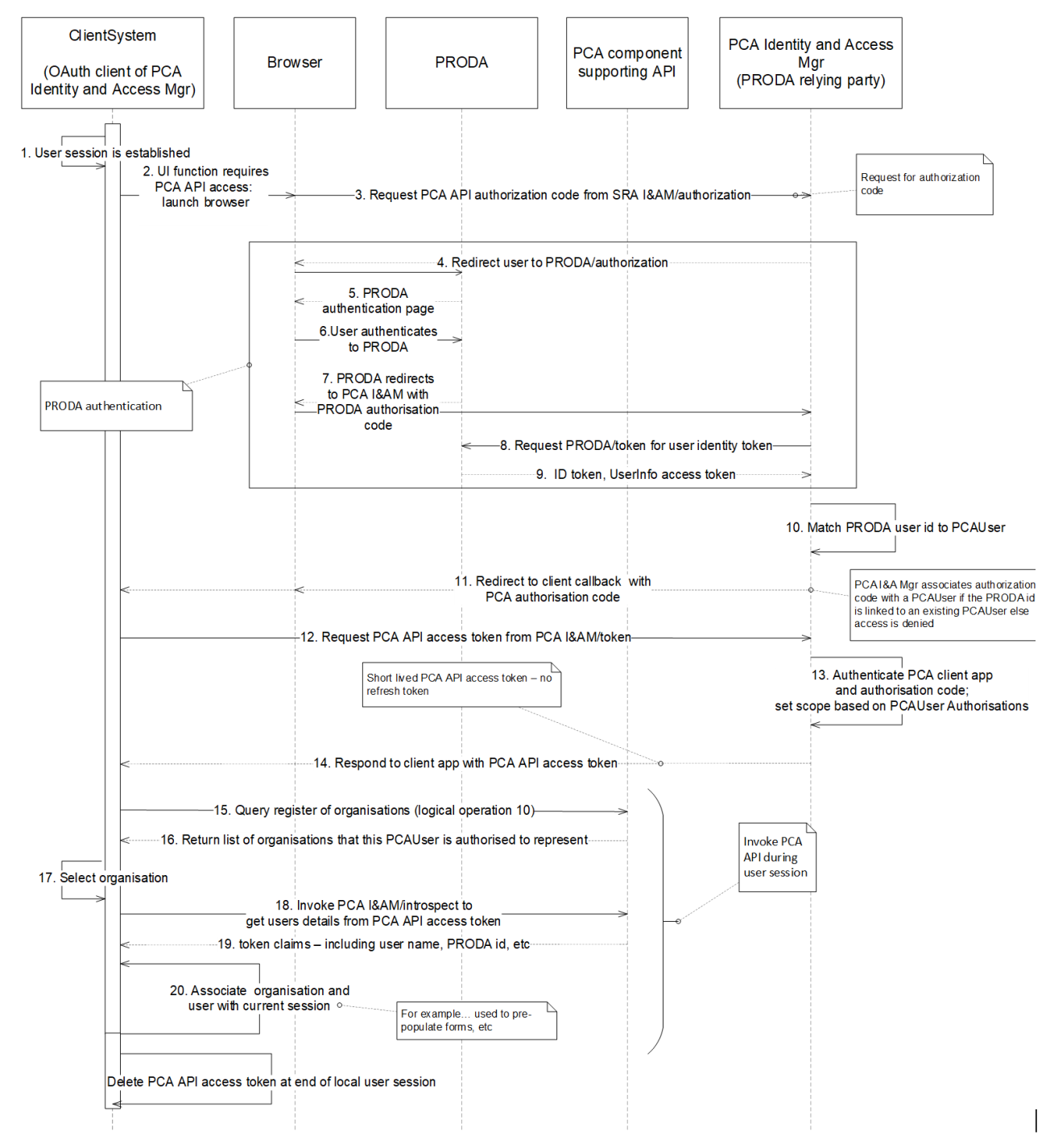
The case where the ClientSystem is the PCA™ Portal, or any similar web application that natively authenticates its users via PRODA, is the same as in figure above except that steps 1 and 2 are replaced by the user navigating with their browser to the web application web site.
Note that the PCA™ Portal is also an OAuth 2.0 client of the PCA™ Identity and Access Manager like all other clients of the PCA™ APIs – i.e. it is also a ClientSystem.

